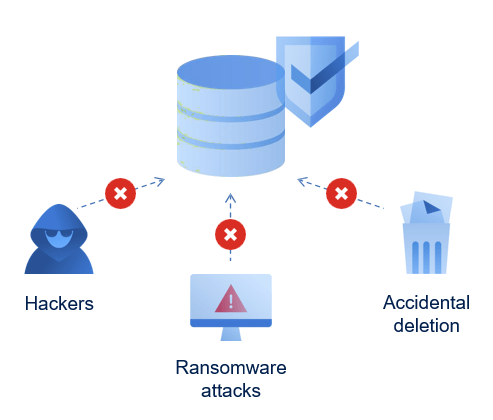
Gain safe and instant remediation without data loss and near-zero RPOs
- Identify important apps on users’ devices.
- Acronis agent tracks changes in these apps.
- In case of malware, restore data from backups.
- Keep users’ work in-progress safe.
- IT controls what gets continuously backed up (e.g., Office files, financial data, images).
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Picture1.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Picture1.png)


![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/cyber-attack-400x400.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/error-400x400.png)


![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Picture2.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Screenshot-2023-11-07-120809.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Screenshot-2023-11-07-122021.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/email-400x400.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/web-security-400x400.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/project-management-400x400.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/backup-400x400.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/disaster-recovery-400x400.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/data-transfer-400x400.png)

![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Picture5.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/Picture6-1.png)
![[alt]](https://presoft.com.my/wp-content/uploads/2023/11/what-is-cybersecurity.jpg)